Like all industries, the oil and gas sector is increasingly faced with cyber attacks. We talked with Edgardo Moreno, industry consultant in charge of cybersecurity at Hexagon about the threats targeting the oil industry, the particularity of the sector and how oil and gas companies can better secure their facilities.
Like many industries, the oil sector is not immune to cyber-attacks and in particular to ransomware and attacks on the supply chain. But unlike other plants, oil and gas facilities are what we call critical infrastructures. Attacks against them, therefore, have by definition critical consequences. This means good protection of the installations is required.

What are the major attacks the oil and gas sector is facing?
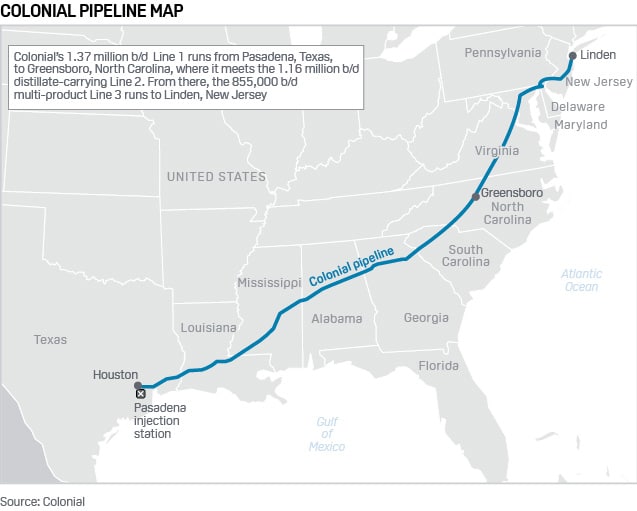
Edgardo Moreno: There are obviously several attacks happening, the most notorious being ransomware. They are the biggest concerns in the industry right now. One of the most famous ransomware attacks in the oil and gas industry was the Colonial Pipeline attack in 2021. The oil and gas industry is part of what we call critical infrastructure. Critical infrastructure is essential for the functioning of our society and for the economy of our countries. This Colonial Pipeline provides nearly half of the gasoline and fuel for the East Coast of the USA. So the impact of such attacks are enormous and can really block our societies.
Supply chain attacks are also very important. You probably remember the SolarWinds attack in 2020. This attack revealed how important it is to secure the supply chain. Attacking the supply chain is very attractive for hackers because by compromising one component of the supply chain, for example, software, you can affect a large number of businesses that are using this software.

What was the impact of the Colonial Pipeline attack?
Edgardo Moreno: The attack itself did not affect the control systems at the facility but the billing system. It blocked the capability of the customers to invoice their bills. But just by compromising this billing system, attackers were able to make the company decide to shut down operations because they did not know at the moment what the extent of the attack was.

What did this attack reveal?
Edgardo Moreno: The attack revealed that the company did not have a very good incident response plan. If they had had a good recovery strategy, they would not have paid the ransom, which they did. If a company pays the ransom, it means that it is not able to recover the data because there is no recovery strategy. So things can be improved here.
Also, right after the attack, the US government set up new requirements for the industry. They issued a guide to compliance that is addressed to any customers working in areas that are critical for the supply and distribution of energy, for example, the pipeline industry. Customers must follow these new guidelines and show they are diligently securing their systems. I think this same kind of initiative will be taken in other industries that are considered critical infrastructure and also in other countries. Unfortunately, we always have to wait until an incident occurs to take this kind of action.

The oil and gas is going digital. How big is the threat now?
Edgardo Moreno: The digital transformation and the need for more digitization mean opening operational systems in the IT network. And this exposes those systems. The oil and gas sector is the industry where the most money can be made out of ransomware. And hackers know that.
And I think, with the war in Ukraine, we are going to see an increase in cyberattacks on critical infrastructure. Whether they are successful or not is another story. But the trend is an increase in attacks.

What is special about the oil and gas sector and what does it imply for the attacks?
Edgardo Moreno: This oil and gas industry is special indeed. Facilities are often huge. One refinery, for example, can supply 20 or 30% of the energy that is used by an entire state or a big part of a country. So by affecting just one huge refinery, you can cause large damage like blocking a part of a country. It is not the same with other industries such as universities and even hospitals. Even if a hospital is hacked, there are others to take care of the patients. But if a huge refinery is hacked, it can cause bigger chaos. Imagine a cyber attack that leads to cutting electricity in an entire state during wintertime! This happened in December 2016 in Ukraine. A malware, which was suspected to be of Russian origin, caused a power cut in the west of the country for 1 hour. It was winter, and a lot of things had to switch on emergency mode. So you can cause a lot of damage just by shutting down the energy supplies. This makes cyber attacks more attractive to hackers because the harm can be enormous.

How can the energy sector better prepare to secure its assets in the event of a cyber attack like ransomware?
Edgardo Moreno: The first step in identifying risk is to gain a comprehensive inventory of industrial assets and critical systems from level 3.5 down to level 0 of the Purdue Model that includes hardware, software/firmware version, and communication module data. It can seem very simple but in the oil sector, it is something that is complicated. The lower the system is stacked on the Purdue model, the harder it is to get the inventory. So this is one of the major challenges for the industry.
Once you have the inventory of your systems, you need to start managing their weaknesses. This includes patch management, risk management, and analysis. Risk management will tell you what technology you need to implement to secure your systems.
You also need to track changes in your systems and your new devices. Change management is not new. The sector has been doing that for physical assets for a long time. But it is more difficult with cyber assets as there are a lot of operational changes so it’s hard to distinguish normal operational changes from changes that could impact security. After that, you can add threat detections and anomaly detections.
These are preventive measures. But you also need to have a good recovery plan, for after you’ve been attacked. You have to know that eventually, you will be compromised. So you need a backup, and a good recovery strategy, otherwise, you don’t have any other choice than to pay the ransom.

Is it more challenging to protect oil and gas facilities than facilities in other industries?
Edgardo Moreno: In the sector, you have extremely old systems running. Some have been operating for 10 or 20 years. Upgrades cannot be done as frequently as it is done in other industrial sectors. That is definitely a challenge for the industry. And the technologies are developed by a lot of different vendors, each with its patch processes, legacy systems, and proprietary configurations. There is no standard protocol. So if you want to do an upgrade, you have to shut down a facility for 3 to 5 months. And that means you cannot produce so you lose money.
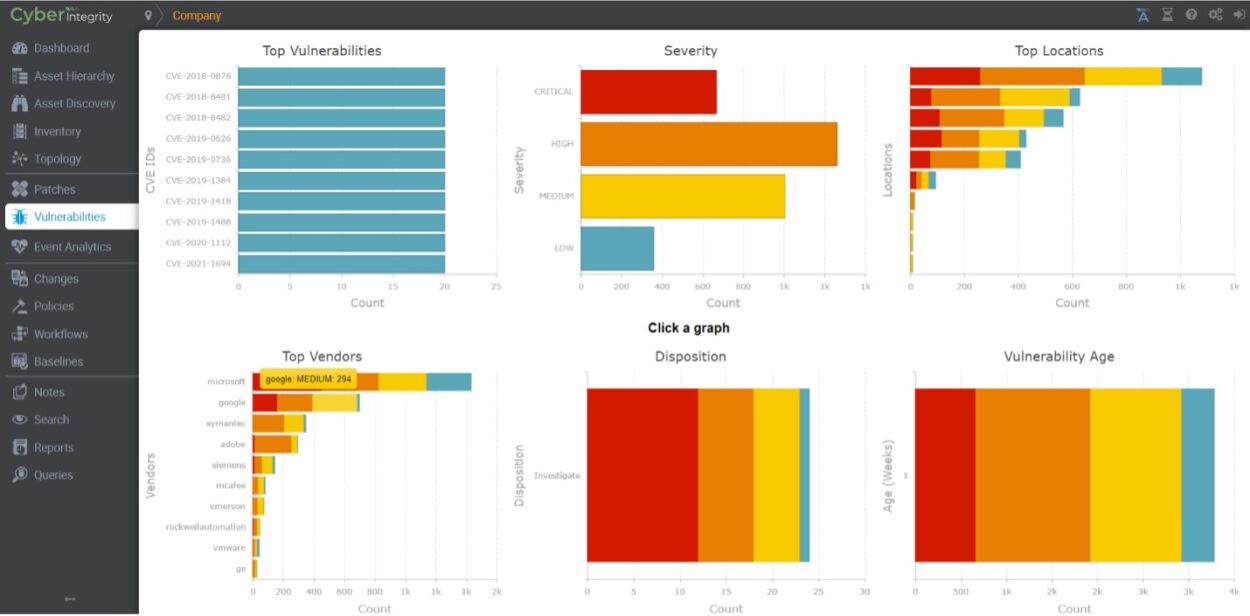

What in Hexagon’s portfolio can help businesses upgrade their systems?
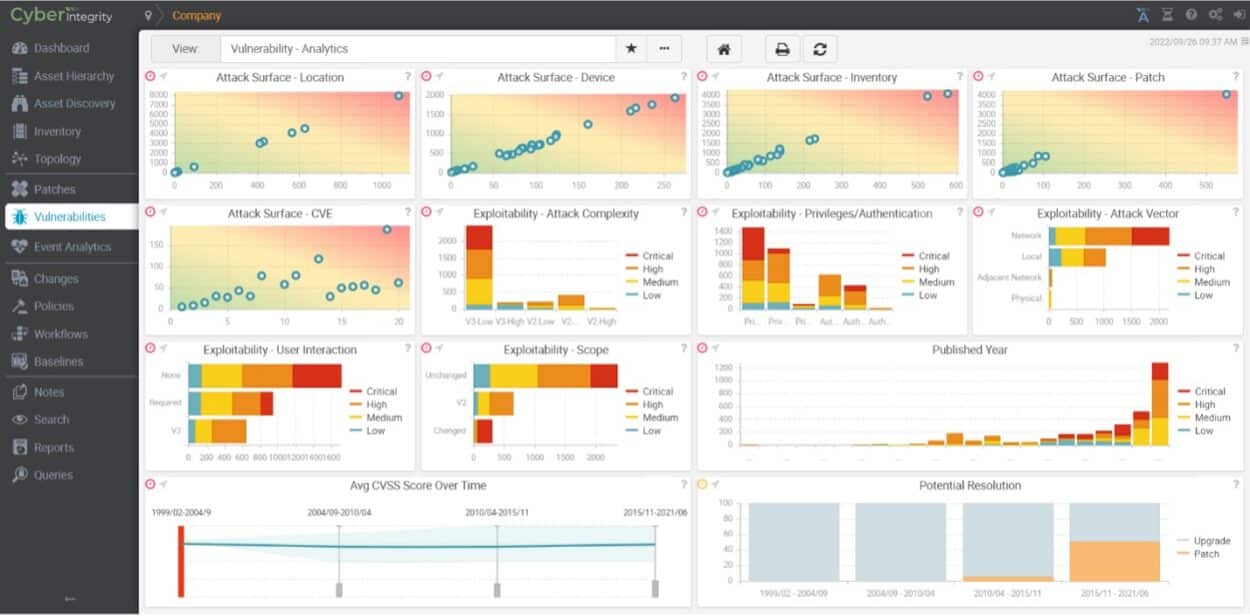
Edgardo Moreno: Hexagon’s PAS Cyber Integrity® enables you to make an inventory of your critical systems including inventorying isolated and transient assets common in OT/ICS environment. It compares the derived OT/ICS asset inventory to known vulnerabilities and maps your attack surface.
With Cyber Integrity you’ll have a centralized, detailed, and comprehensive vulnerability management solution that is a reliable resource for vulnerability assessments, patch planning, and risk assessment activities. Once you know the most important vulnerabilities to remediate or mitigate first, you can adjust your security posture by considering the probability and consequence that a vulnerability could be successfully exploited within your environment. You will be able to calculate a risk score that will let you know where to focus your resources to reduce risk.
We also offer the ability to both track and manage changes, when you turn off a facility and you start making changes to your physical systems (pipes, cabling…) and to your cyber assets. We allow our customers to make snapshots of their network configurations before changes are made and then confirm these changes after the work is done.