The Cybersecurity Conference “Les Assises de la Cybersécurité” was held last week in Monaco. Cybersecurity experts and major industrial players gathered for 3 days to discuss the new threats in cyberspace and how companies can better secure their assets. DirectIndustry e-magazine was invited to cover this event. One of the major themes discussed this year was the attacks on the supply chain, which are on the rise.
Cyber attacks are intensifying. As companies are increasingly going digital to improve their productivity (the trend has been accelerated even more with the COVID-19 pandemic), they are also increasingly falling victim to cyber-attacks. And one of the new trends is attacks on the IT supply chain.
“Attacks on the Supply Chain Have Increased Twofold”
An IT supply chain attack aims to damage targeted companies by attacking the least secure elements of their application supply chain, for example, by infiltrating a Trojan horse through software produced by one of their vendors. As companies are using more and more various software from various vendors, this trend is accelerating.
According to Paul Rascagnères, Global Research and Analysis team (GReaT) at Kaspersky,
“Attacks on the supply chain are increasing. Attackers target the vendors and not directly their target because this target is harder to attack on the front end. Today the ecosystem is complicated: companies have different servers, laptops with multiple applications, phones with multiple applications, and various devices within their infrastructure. In the end, businesses have a huge number of vendors that they trust. The attacker comes in the middle of this chain of trust.”
According to Olivier Ligneul, President of Les Assises and CISO for French energy provider EDF,
“Attacks on the supply chain have increased twofold since 2019.”

The SolarWinds attack is one of the most notorious recent events. Texas-based software company SolarWinds came under an undetected cyberattack in September 2019 with hackers gaining access to the production system for Orion, SolarWinds’ flagship software. The problem was that the software is used by thousands of businesses and organizations around the world. Hackers were, therefore, able to infect Orion’s users and access their computer networks without being detected. Of the 18,000 infected customers, about 100 were infiltrated, including government entities.
More recently in July 2021, the much-discussed Kaseya ransomware attack occurred. Kaseya is a provider of IT management software for MSPs and small to medium-sized businesses. This summer, attackers identified and exploited a vulnerability that allowed them to compromise Kaseya’s Virtual System Administrator solution, which is used to remotely monitor and manage endpoints and servers. The hackers released a fake software update containing ransomware to all managed endpoints. As with the SolarWinds attack, the malware spread among Kaseya’s clients and affected dozens of businesses forcing some of them to stop their activities. The attackers demanded that Kaseya pay a staggering $70 million in ransom to restore the data of the affected customers.
What Are the Strategic Advantages of This Type of Attack?
For Paul Rascagnères, attacks on the supply chain can have two strategic advantages:
“First, this type of attack allows your attacker to get into your system via your provider because your provider has a lower level of security than you do, so it is easier for him. And there is another advantage. If your provider has thousands of customers worldwide, with only one campaign the attacker targets thousands of customers at once. In terms of return on investment, it’s super profitable.”
And given the effectiveness of this type of attack, Paul Rascagnères expects to see more of them in the future:
“That’s the problem of the future because we’re more likely to increase our suppliers than to decrease them. The attack surface when you have 1,000 suppliers is so big that you can’t defend it. This plays to the advantage of the attacker and it is difficult to fight for the defender.”
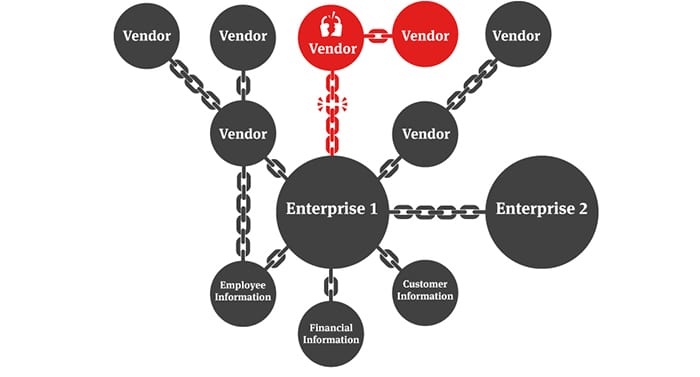
What to Do When a Supplier is Compromised?
In the event of such an attack in an ecosystem, what should be done? Guillaume Poupard, CEO of ANSSI, the National Cybersecurity Agency for France, believes that the information that one vendor has been attacked should not be disclosed so as not to aggravate the situation for the victim. An organization that has been attacked may have difficulty operating or even surviving, and publicly disclosing this kind of information could be the fatal blow.
But for Olivier Ligneul, there needs to be a balance:
“A balance must be found between not disclosing public information about the victims so as not to aggravate their situation and at the same time warning those close to the ecosystem that a link is attacked because it may be the entire ecosystem that is under attack. We need to put in place governance mechanisms in which we agree on how to disseminate this type of information and put in place contractual mechanisms and build relationships with all those involved so that information circulates without becoming too public.”
France has put into place a network of CERTs (Computer Emergency Response Team). These official bodies are responsible for providing risk prevention and incident handling services. They could also be useful for coordinating operational mechanisms and communicating information between those concerned so as to protect the whole ecosystem without publicly harming the compromised one.
“At the moment, we are building links with the different parties because we all need to know each other to be able to coordinate. We all agree that this is imperative. This allows us to put in place mechanisms for incident response processes. For example, it allows us to know who to call in case of a problem. A supplier that is compromised can be the supplier of different members of an ecosystem, so we must be able to link a supplier to the different sectors affected in order to coordinate cross-sectorally. This adds a level of complexity at the national and international level.”
How to Protect Yourself?
Before agreeing on a coordination entity to inform the entire supply chain in France and abroad, there are a few things you can already put in place to protect yourself, explains Paul Rascagnères, on the hardware and on the software sides:
“For hardware, when we have a new system, we don’t hesitate at GReaT to run our machines with no load, to make network captures for days, for weeks. This allows us to see what is happening on the machine before installing anything on it. This allows us to detect any possible anomalies and see if the machine connects to servers that have a dubious reputation.
He also recommends
“Imposing on suppliers that their applications be signed. Today in 2021, you can’t check that your vendors are delivering applications that are signed. You can’t verify that they are coming out of their build chains.”
On the software side, Paul Rascagnères recommends limiting the number of suppliers without really believing it can be achieved as the trend proves to be the opposite.
One last recommendation to businesses would be not to display the name of their suppliers on their website and avoid being displayed as a customer of a solution. Criminals know how to use Google and releasing too much information offers potential attackers an important advantage.