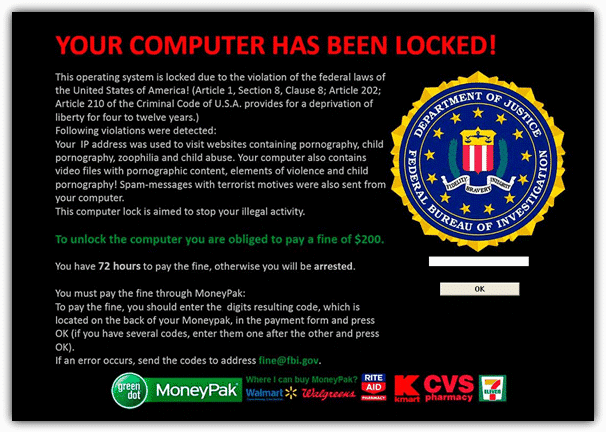
Last month, more than 126,000 people in more than 100 countries were victims of a massive worldwide ransomware attack, a form of hacking designed to encrypt the target’s data pending payment of a ransom. The WannaCry cyberattack infected U.K. National Health System, Spanish Telecommunication company Telefonica, French Automaker Renault, and German railway company Deutsche Bahn. Last year, the San Francisco Municipal Transport Agency was the victim of a ransomware attack. DirectIndustry e-magazine investigated this increasingly-common form of cyber attack.
In 2016, San Franciscans took 725,000 daily trips on Muni, the municipal transport system famous for its cable cars. However, on 25 November, some of those seeking to travel found themselves unable to pay fares using Muni ticket machines. The San Francisco Municipal Transport Agency (SFMTA) had fallen victim to a ransomware attack.
The attack affected only office computers, but the SFMTA turned off ticket machines and fare gates as a precaution. The organization said in a statement:
“This action was to minimize any potential risk or inconvenience to Muni customers. The primary impact of the attack was to approximately 900 office computers. The SFMTA’s payroll system remained operational, but access to it was temporarily affected.”
Nonetheless, this disruption to the seventh largest transport system in the US demonstrates the threat from ransomware attacks to industrial companies and offers a few lessons.
The Birth of a New Threat
Ransomware can infect systems in the same way as any other malware: through malicious payloads attached to emails, phishing scams and direct breaches of network security. Any organization can fall victim to such attacks, but industrial companies should be aware of the potential for hackers to exploit control and engineering systems with ransomware. According to Tim Erlin, vice president of product management and strategy at Tripwire, a software company that helps detect security vulnerabilities:
“Whereas industrial systems relied on proprietary technology in the past, there is a general market trend for greater connectedness and more use of standard protocols. This makes them more exposed to the risks inherent in these technologies.”
He added that the trend toward connecting older, proprietary technologies to networks offers hackers increased opportunities to exploit their potential vulnerabilities.
Although no cases of ransomware attacks on industrial systems have come to light, researchers at the Georgia Institute of Technology have developed PLC ransomware to find ways to counter it.
According to a paper published in February 2017,
“Industrial control system networks have so far remained largely unscathed by malware, not because they are more secure than traditional networks, but because cybercriminals have yet to figure out a profitable business model to make such attacks worth their time. Recent attacks on hospitals have demonstrated how profitable ransomware can be when used to hold operationally critical assets hostage with the threat of human harm, and reports suggest attackers are beginning to shift their focus to ICS networks.”
Spotlight on Attractive Targets
Manufacturing is already the second most common ransomware target, behind the services sector. It is the target of 17 % of attacks, while construction suffers 4% of attacks and transport, utilities and communications get 7%, according to research by security technology firm Symantec.
Andrew Wadsworth, cybersecurity expert with PA Consulting, says energy, rail and other infrastructure providers could prove lucrative targets for hackers using ransomware to exploit industrial control systems. The perpetrators of these attacks need not necessarily be experts in industrial systems, as these technologies often rely on standard systems, such as Cisco switches and Windows servers, he says.
“I suspect that ransomware attackers will go where the money is. They have not necessarily figured out how much money they could make from industrial firms, but if they see that they can cause significant impact, then these companies become attractive targets.”
Industrial companies vary in how well prepared they are.
“Some do daily anti-virus updates on their control system because they have been built to do that. But there are a lot of legacy systems which are not easy or possible to update in that way because they are a generation out of date. The lifecycle of control systems is longer than general IT systems and there is still a lot of legacy out there.”
However, the slow pace of change favors a security technique called whitelisting, which limits systems to running only approved services and applications. In general, whitelisting has been slow to take off, as it can be difficult to manage in complex, fast-moving IT environments. In industrial control systems, there is less complexity and slower change, so whitelisting could prove an efficient and effective defense against ransomware attacks, Wadsworth adds.
“The technique is underused, but it’s a very elegant solution in this case.”
Meanwhile, industrial firms are well advised to pay attention to basic “security hygiene” to prevent attacks, says Tripwire’s Erlin. They should ensure software patches are up to date, monitor networks for signs of intruders and regularly change passwords.
While it is no defense against attacks, backing up data can make them less effective. The SFMTA was grateful it had the backup systems to restore its computers within a couple of days.
“The SFMTA never considered paying the ransom. We have an information technology team in place that can restore our systems.”
But for many industrial control systems, a couple of days might be 48 hours too late.